Maximize ROI.
Minimize Waste.
I’ve worked with many cybersecurity firms, but this one is just right. Their comprehensive pen testing revealed vulnerabilities we quickly remediated, with detailed, actionable reports. Proactive and relationship-focused, they treated us like a top client despite our small size. Enhanced our security posture immensely—highly recommend!
Cynexlink has lifted the burden of patching, security, and maintenance from our IT team, ensuring 24/7 uptime for our construction ops. We now focus on strategic growth and faster implementations—systems are always ready, empowering our 24/7 workforce.
Trusted & Proven




Trusted IT Security Experts

3 Step To A Fully Secured Business
Let Cynexlink help you take control of your cybersecurity with a smart, simplified approach.
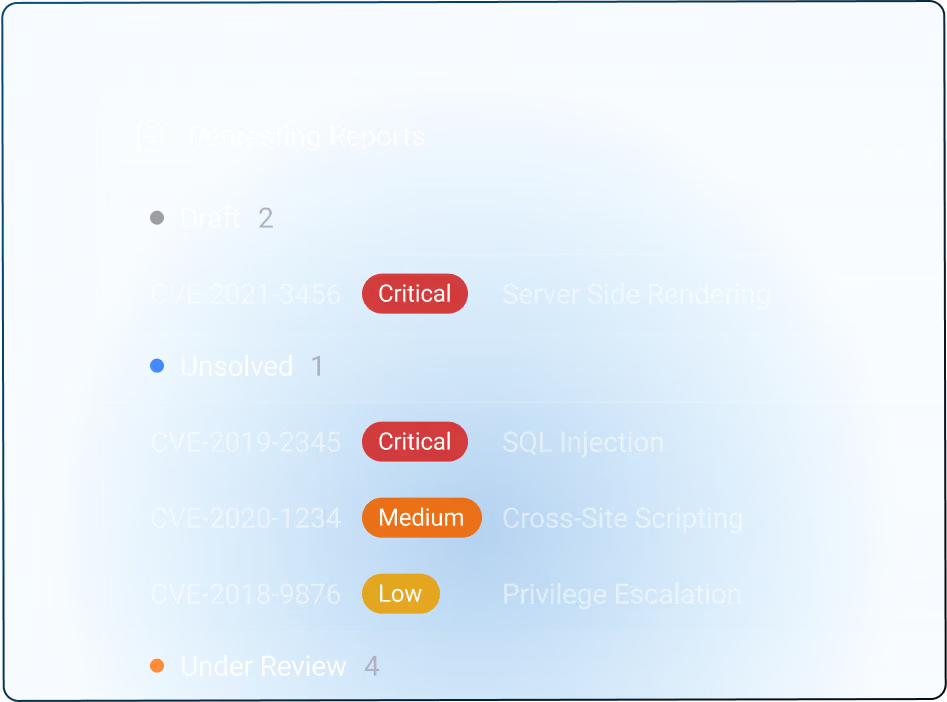
Our Cybersecurity Audit uncovers the hidden gaps in your systems and verifies that your system is actually working to protect your clients and your business.
.avif)
Identify and prioritize risks across your systems, networks, and endpoints.

We'll build a Cybersecurity & IT Roadmap around your company's goals and risk profile
The Services We Offer
Explore our comprehensive and customizable suite of services....
Seamless Cloud Management for Your Entire Infrastructure
Your cloud environments — storage, applications, servers, and data — are essential. Our Cloud Services optimize them. We provide scalable solutions that ensure reliability, performance, and easy integration for your business growth.
Your cloud data — applications, networks, users, and storage — is vital. Our Cloud Security service safeguards them. We deliver advanced threat detection and zero-trust architecture to prevent breaches and ensure secure access in real-time.

Your operations — policies, audits, data handling, and processes — must comply. Our Compliance & Frameworks service supports them. We offer tailored strategies for standards like HIPAA, CMMC, and GDPR to minimize risks and streamline certifications.

Your endpoints — laptops, desktops, mobile devices, and servers — are crucial. Our Endpoint Protection service defends them.We provide a strong EDR solution that identifies threats in real-time and helps you respond.

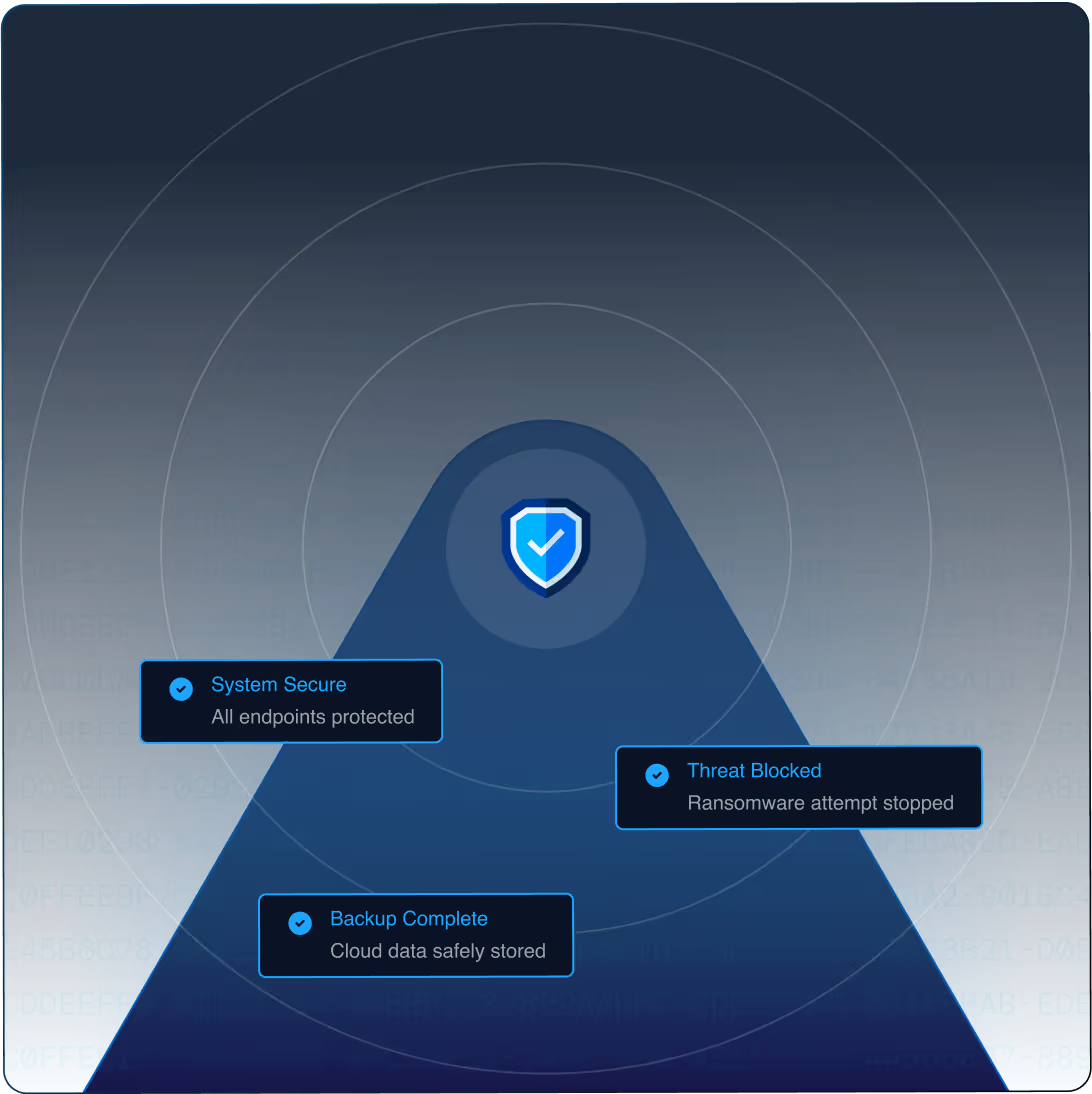
Safeguard Your Business Operations












Smarter IT. Stronger Security. Seamless Support.




%201.svg)



Secure Every Digital Asset


Latest Episodes
Latest News: Breaking Cybersecurity Trends
Types of Phishing Attacks Explained
Learn the main types of phishing attacks, how they work, and why phishing remains one of the most effective cyber threats today.

What Is Phishing? A Complete Guide to Modern Phishing Attacks
Learn what phishing is, how modern phishing attacks work, common techniques attackers use, and why phishing remains one of the biggest cyber threats.

Cybersecurity in 2025: A Year That Redefined Digital Risk
Cybersecurity in 2025 exposed a major shift in attacker strategy — away from fast ransomware and toward persistent, infrastructure-focused compromises.



.png)
.png)
.png)
















